As we are securing our house, before we leave, close all the doors and windows, but yet unaware that we forgot to close our front door on our way out
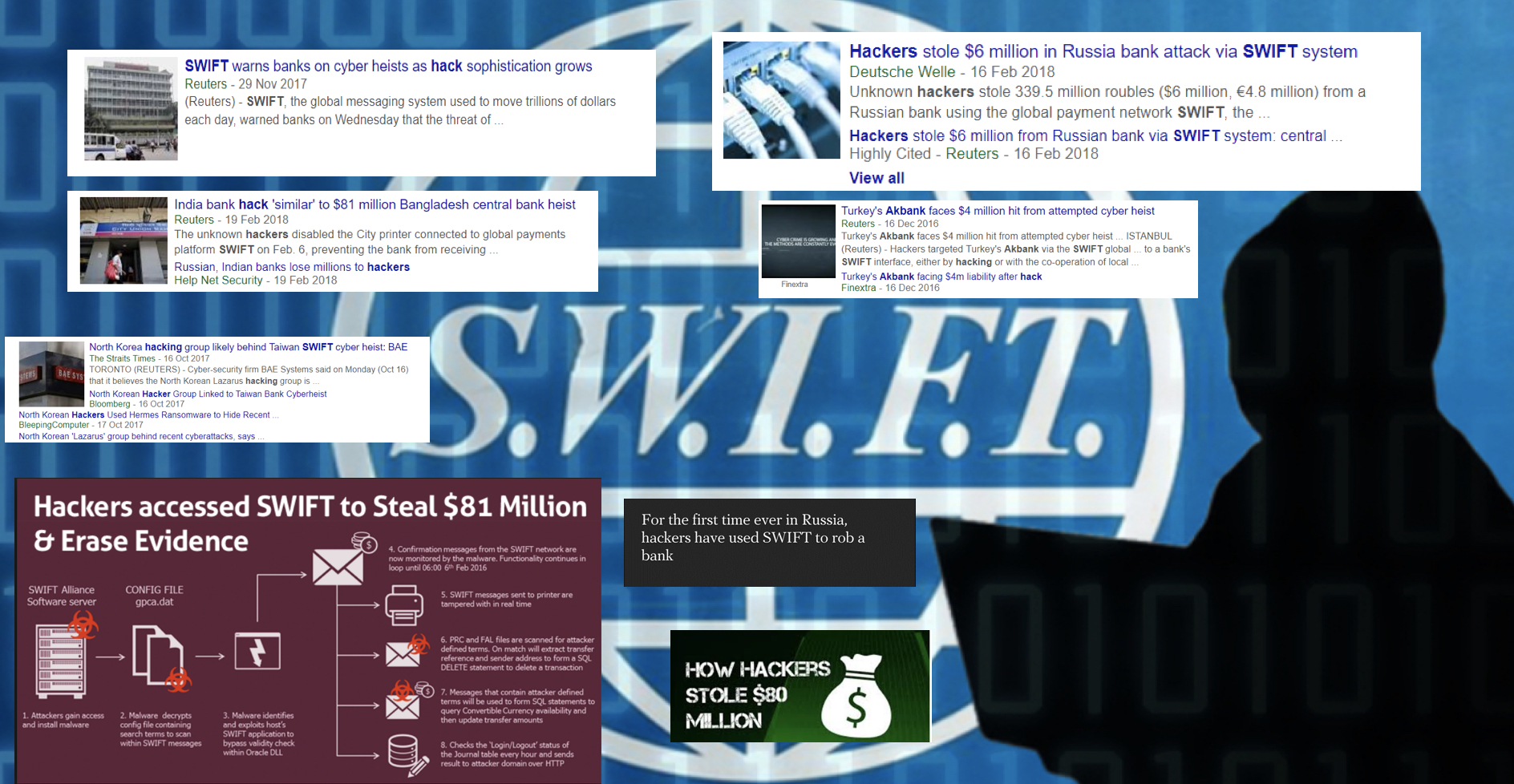
Increasing cyber-attacks and recent instances of payment fraud in customers’ local environments demonstrate the necessity for industry –wide collaboration to fight against these threats. Therefore, The Society for Worldwide Interbank Financial Telecommunication (SWIFT) has established the Customer Security Program (CSP) to support its customers in the fight against cyber-fraud targeting their SWIFT-related infrastructure. SWIFT confirms new cyber threats, due to an increasing sophistication and frequency of cyber-attacks that are encouraging governments, banks and other players to re-evaluate their security measures. https://www.swift.com/myswift/customer-security-programme-csp
As it always is with these frameworks from regulators or suppliers; the CSP is not optional whether you want to comply to this framework, it’s mandatory! Let us first begin with understanding what the CSP is and then what we need to do.
The Customer Security Program
The SWIFT CSP focuses on three mutually reinforcing areas:
- Protecting and securing your local environment (You),
- Preventing and detecting fraud in your commercial relationships (Your counterparts)
- Continuously sharing information and preparing to defend against future cyber threats (Your community).
While all customers remain primarily responsible for protecting their own environments, SWIFT’s CSP aims to support its community in the fight against cyber-attacks and ensure a consistent and effective approach for the management of cyber incidents.
Security Controls
Issued set of security controls are articulated around three overarching objectives: ‘Secure your Environment’, ‘Know and Limit Access’, and ‘Detect and Respond’ which, in turn, are linked to eight security principles and twenty-seven controls These twenty-seven controls comprisedof 16 mandatory controls and 11 advisory controls. The controls have been developed based on analysis of the latest cyber-threat intelligence and in conjunction with industry experts. The CSP security controls have also been mapped to the following 3 international security standards: PCI-DSS, ISO 27002, and NIST.
All users must self-attest compliance against the mandatory security controls, irrespective of whether they connect to SWIFT directly or indirectly. The remaining advisory controls may be required later. The SWIFT Customer Security Controls Framework document describes the different technology footprints and architecture types and indicates in-scope components. Depending on the architecture type, more or less security controls are applicable.
The Customer Security Attestation Process (CSAP) is designed to incentivize genuine improvements in security across the community; it is not a ‘tick-box’ exercise. The approach fosters transparency between SWIFT users to strengthen security.
What is the impact of CSP on users?
The Security Attestation Application always indicates the date on which a self-attestation was published. In principle, a published self-attestation is valid for a 12-month period commencing on the publication date. At least every 12 months, a self-attesting user must publish a new self-attestation. The Security Attestation Application is designed to trigger automatic notifications to users prior to the expiry date of a published self-attestation. The attesting user must also submit a new self-attestation if there are other material changes in circumstances, such as a change in architecture type, change in service provider, or a change in the security controls compliance status. Each bank’s attestations will be available to the other banks on the network.
Much of the SWIFT Controls Framework is a well-tread ground from a security perspective, but more interesting and novel is the method it uses for compliance reporting and enforcement. Banks have to sign onto SWIFT’s “Know Your Customer” portal and show compliance with the controls framework. As said, this is not a ‘tick-box’ exercise, one needs to show compliance to Test the Design and Operating Effectiveness of the controls!
SWIFT says that each user is responsible for the correctness and completeness of its own attestation. This is key to support proper counterparty risk management and business decision making processes. Moreover, they may also be required to provide a more detailed proof of compliance.
SWIFT will follow up and not they are not Alone!
To support the effectiveness of the Customer Security Controls Framework, SWIFT reserves the right to report to supervisors (DNB ECB, etc.) and others, as applicable, the names of users that fail to complete their self-attestation or fail to comply with all mandatory security controls by the relevant deadlines. Reporting to supervisors and others starts in 2018 and will continue on an annual basis.
- From January 2018, SWIFT reserves the right to report users that have failed to submita self-attestation.
- From January 2019, SWIFT reserves the right to report users who have failed to complywith all mandatory security controls (or who connects through a non-compliant service provider such as service bureau offering SWIFT connectivity).
- For users that are not supervised, identical circumstances and data may be reported by SWIFT to their messaging counterparts.
Complying with the SWIFT Security Controls Framework may be harder than you think
The framework includes requirements around identity and access management, vulnerability and patch management, and other fundamental security processes that should already be prioritized across every institution. From a security perspective, the framework isn’t significantly different from other regulatory requirements, especially in the financial services industry. That is not to say that compliance will be easy for many members, especially the organizations which have low maturity on IT Governance, Risk Awareness and Risk Management.
According to my own research, during implementation of the CSP program and the its attestation processes, following issues were noticed by the experts:
- Current security processes and control frameworks of organizations may not be enough to comply or fully integrate able with SWIFT CSP Framework. Moreover, existing framework may need to be revisited to prevent complexity. For example, Cyber-threat intelligence-sharing may not always be an explicit regulatory requirement, but it is encouraged.
- SWIFT CSP Framework may be considered as an IT Security Program only. Not all required experts were informed and aware of the framework importance. SWIFT framework requests multidisciplinary, company-wide effort. Moreover, differences in perspectives can make it difficult for people to communicate risk and compliance aspects.
- There isn’t always sufficient SWIFT related knowledge in the organizations:
- SWIFT security requirements are not translated properly to the related stakeholders and business units;
- Besides the technical requirements, configuration of the SWIFT components needs input also from business units;
- Spending money on solutions is a waste if no one knows how to implement the control and check its efficiency and effectiveness properly (or, in the case of outsourcing, auditing the solution provider and holding them accountable). For example, an organization considers that their logging controls do not meet the requirements for logging and monitoring and therefore invests in logging tools solely;
- organization needs someone with SWIFT expertise, even if you plan on outsourcing management of SWIFT.
- Organizations falsely consider that self-attestation is a one-time practice only, however attestation is valid only for a 12-month period. The organization actually needs to be and to show continuously that it is in control.
How you can get fit for SWIFT CSP
For a secure SWIFT environment, organizations should keep in mind that:
- The attestation should not be seen as a comply/not comply sign-off. Drilling down to specific controls is needed. Again, it is not ‘tick-box’ exercise, it’s showing that the controls are operating effectively.
- SWIFT CSP Framework has to be integrated to the organization’s existing framework. Ensure that all of the related SWIFT CSP implementation guidelines are taken into consideration by experts. I-Inc has an Integrated IT Governance Control Frameworks covering the entire IT domain that is mapped to all relevant control frameworks out there, including SWIFT CSP. Based on this framework on organization can “test once” of IT controls “and comply to many” to IT control frameworks that are used by supervisor and regulatory institutes.
- The importance of the framework and attestation process has to be communicated to the organization and different teams have to be involved in implementation and attestation processes. Successfully implementing and maintaining controls often means an organizational and behavioral change. SWIFT Security isn’t just one person’s or team’s responsibility. IT, Human Resources, Business, Security, SWIFT experts should be included to process. Moreover, proper established Relationship Management Application (RMA) and Know your Customer (KYC) process has an important role to play with in secure SWIFT environment.
- If you use a Service Bureau, find out what level of protections they offer.
- The SWIFT knowledge in the organization must be increased. A small misconfiguration can cause serious damage, as has been shown in practice.
- A continuous follow-up process must be created so that the attestation is transparent effective and efficient.
Good luck getting where you need to be!
This Blog was written by guest writer Serkan Kaplanoglu. Serkan is an IT Audit, Risk and Security expert with extensive knowledge of and experience in SWIFT. Serkan wrote this article on his on title.
For more information, please contact us at info@i-inc.nlor check our website www.i-inc.nl